Hello,
In this article I’ll present you my solution on the Chapter 5 CTF from the book Practical Binary Analysis.
For this binary, the hint is to fix four broken things.
Running file gives us the following response:
| |
And the readelf command gives us:
| |
At this moment, it was clear that the ELF header is broken, in order to fix it I opened up Wikipedia and the elf specification.
As I went through each field manually, with Binary Ninj. As I was checking the offset of the current byte, at 0x07, Wikipedia says: It is often set to 0 regardless of the target platform. I’ve changed it to 0x00. (Note: I think this field was probably ok as it is)
At offset 0x12, the value Specifies target instruction set architecture and is currently invalid. From googling, I found an article titled: Novell's Next Generation OS Will Natively Support Intel's Future IA-64 Architecture so I set the value to 0x3E.
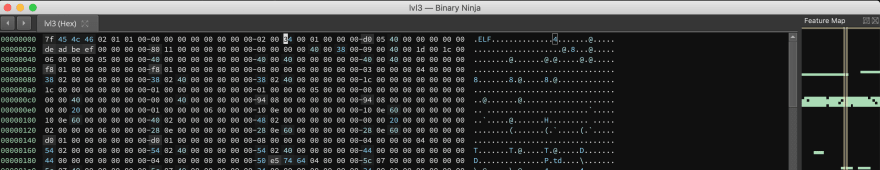 At offset 0x20 we have the
At offset 0x20 we have the e_phoff which Points to the start of the program header table. It usually follows the file header immediately, making the offset 0x34 or 0x40 for 32- and 64-bit ELF executables, respectively. The value de ad be ef is clearly invalid. I replaced the value with 40 00 00 00.
At this moment I thought I fixed the binary and ran it, it ran and it gave me an invalid flag.
If you run the following command:
| |
You’ll see that the .text section is marked as 0x8 - NOBITS and it should be 0x1 - PROGBITS. To make the change I’ve used Binary Ninja as a hex editor, opening the binary in raw mode.
From the readelf command:
| |
The start of the section header is 4480 bytes. A section header has the length of 0x40 bytes. 4480 to hex -> 0x1180. 0x40 * 14 + 0x1180 = 0x1500.
At offset 0x1504 we change the type from SHT_NOBITS to SHT_PROGBITS.
After we run the binary we get the valid flag:
| |
After finishing level 3 I wanted to go to sleep and instead I thought of running ltrace, strace on the binary and I got this:
| |
Didn’t expect this, very nice tho.
Thanks for reading!