Hello!
My daily work is doing full stack web development, and reversing is a side thing that I do for fun and in my free time. In this article I will show you an easy way to solve for ELF C++ – 0 protection challenge, which can be found on https://www.root-me.org under the cracking section.
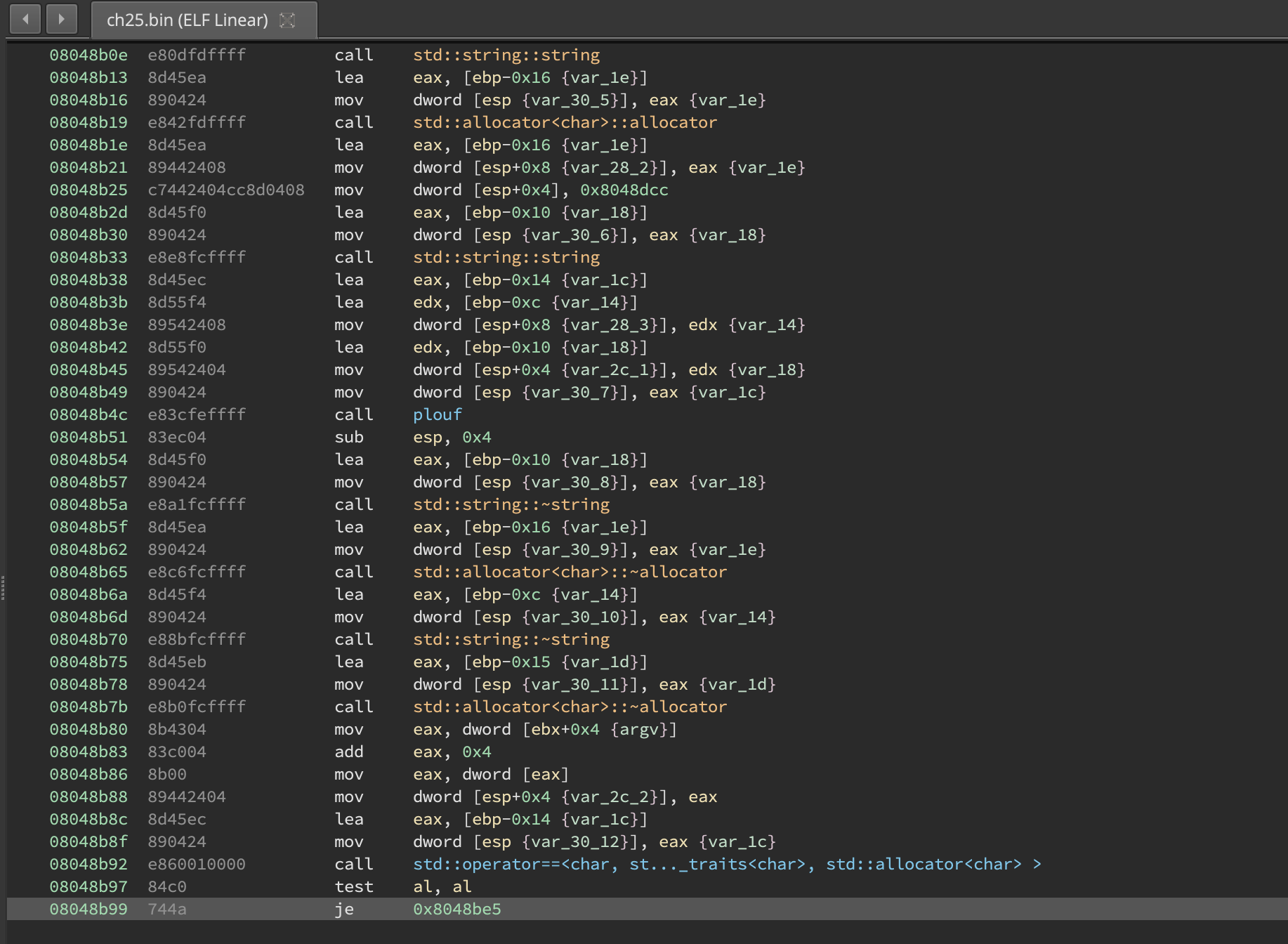
I found this challenge a bit difficult mostly because I’m not used to reverse C++ code but, since it doesn’t contain any protection at all, all you need to do is to inspect the parameters.
 If we play with the binary a little, maybe visualize it in
, we can see that plouf is an interesting function and it’s definitely doing something, like decoding something from the binary and constructing a string.
If we play with the binary a little, maybe visualize it in
, we can see that plouf is an interesting function and it’s definitely doing something, like decoding something from the binary and constructing a string.
If we fire gdb and run the program, we can setup a breakpoint right after plouf and inspect the returned value.
| |
gdb ch25.bin r 123 b *0x08048b51
x/10x $eax 0xbffff664: 0x1c 0xc1 0x04 0x08 0x2c 0xc0 0x04 0x08 0xbffff66c: 0x14 0xc0
| |
This doesn’t tell us much, but if you look closely you can see that it points to: 0x1c 0xc1 0x04 0x08
Which is an address: 0x0804c11c it is written that way because of endianness. Inspecting the value of the address in GDB will give us the output that plouf spits.
PS: Things get even more easier if you’re using GDB Peda.
Resources:
Thanks for reading!